In 2005, the topic of supply chain vulnerability was still a relatively unexplored territory, though it was already in its ascendancy to becoming one of the major areas of management research. In her article Drivers of supply chain vulnerability: an integrated framework, Helen Peck identifies four drivers of supply chain vulnerability, based on an exploratory and empirically grounded case study of commercial supply chains.
In 2005, the topic of supply chain vulnerability was still a relatively unexplored territory, though it was already in its ascendancy to becoming one of the major areas of management research. In her article Drivers of supply chain vulnerability: an integrated framework, Helen Peck identifies four drivers of supply chain vulnerability, based on an exploratory and empirically grounded case study of commercial supply chains.
A multi-level framework for analysis
The case study, which is minutely detailed in the paper referenced below, suggests that the sources and rivers of supply chain vulnerability, and conversely, supply chain resilience, are found at four different and interlinked levels within the supply chain:
Level 1 – Value stream, product or processes
Workflows and information flowsLevel 2 – Assets and infrastructure dependencies
Fixed and mobile assetsLevel 3 – Organizations and inter-organizational networks
Contractual and trading relationshipsLevel 4 – The Environment
Social and natural environment
Intertwined and connected
In assessing the vulnerability of a supply chain, all levels should be investigated in how their characteristics influence the supply chain.
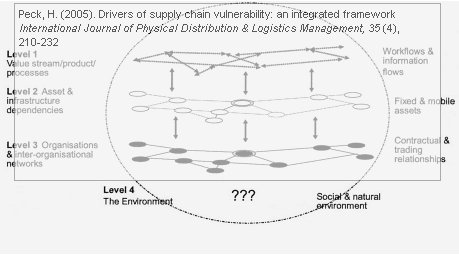
At level 1, the supply chain is seen as a logistics pipeline, where the focus on lean and agile practices have made supply chain performance the overall goal but at the same time it also exposed the supply chain to many risks.
At level 2 the focus is on the supply chain as a carrier of goods and information, and supply chain vulnerability is determined by production sites, distribution centers and warehouses, as well as IT and other communication facilities, and also the whole transportation network from supplier to end customer.
At level 3 the view is further afield, looking at the supply chain from a strategic and management perspective, where organizational management, power-sharing, collaboration and competition become important factors in evaluating vulnerability.
At level 4 the view is a broad macroeconomic perspective, political, economic, social, legal and technological factors, and disruptions or sudden changes in these factors are more often than not beyond the control of the company, but must be dealt with accordingly.
Conclusion
The 4-level model employed by Peck is an excellent tool for explaining the scope and dynamic nature of supply chain risk. It emphasizes that a resilient network involves much more than the design and management of robust supply chain processes. It is important to recognize that by taking actions to reduce risk at one point within the four levels, at the same time the risk profile for the other levels is changed, including players and stakeholders not thought of in the initial risk assessment. Supply chains are dynamic and constantly evolving, and so is supply chain risk. Achieving supply chain resilience is a constant battle and a never-ending process.
References
Peck, H. (2005). Drivers of supply chain vulnerability: an integrated framework International Journal of Physical Distribution & Logistics Management, 35 (4), 210-232 DOI: 10.1108/09600030510599904
Links
- linkedin.com: Dr. Helen Peck