 This week’s focus are risks in the maritime supply chain. Today’s article reflects on security in maritime supply chains: Assurance of security in maritime supply chains: Conceptual issues of vulnerability and crisis management by Paul Barnes and Richard Oloruntoba from the Queensland University of Technology in Brisbane, Australia, suggests that the complex interaction of ports, maritime operations and supply chains creates vulnerabilities that requires analysis that extends beyond the immediate visible.
This week’s focus are risks in the maritime supply chain. Today’s article reflects on security in maritime supply chains: Assurance of security in maritime supply chains: Conceptual issues of vulnerability and crisis management by Paul Barnes and Richard Oloruntoba from the Queensland University of Technology in Brisbane, Australia, suggests that the complex interaction of ports, maritime operations and supply chains creates vulnerabilities that requires analysis that extends beyond the immediate visible.
Do rules and regulations work?
A critical factor for international business is the assurance of security across maritime trading systems and a number of initiatives, first and foremost ISPS, CSI and C-TPAT have been put in place to reduce or avert maritime terrorism, but are these initiatives actually working as intended and are they even having a negative impact on competitiveness ?
ISPS, CSI, C-TPAT
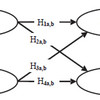
What this article has made perfectly clear to me is the difference between ISPS, CSI and C-TPAT and how they interact and relate to not only the maritime supply chain, but to the supply chain in full, including the supplier or producer (“pre customs”) and the customer (“post customs”):
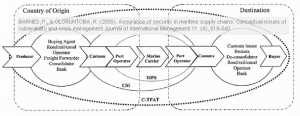 Click image for larger version
Click image for larger version
What the figure also highlights is that there is a complex interaction between these initiatives, and governments imposing these initiatives on businesses do not always consider the wider financial and social impact of compliance with these regulations. Yes, it may reduce the likelihood of terrorist-related incidents, but it also adds costs to doing business, cost that more often than not are a hinder for competitiveness. In essence: the initiatives lack the necessary balance between the requirements for efficiency and security in the supply chain.
Maritime security issues
In maritime supply chains there are mainly three attack points or penetration points that can contribute to security problems:
Cargo: Using cargo to smuggle people or weapons.
Vessel: Using the vessel as a weapon.
People: Using fraudulent identity to gain access to vessel or cargo for the above.
The authors do not mention this, but I would think that this classification scheme applies not only to maritime supply chains, but to the other modes of transport as well, you just have to replace the vessel with the according carrier.
The (overlooked) economic impacts of maritime security threats
International trade relies heavily on safe and open waterways and oceans, including ports, so the authors say.
Maritime security threats and and the plethora of other threat sources introduce high levels of uncertainty to business considerations and the world economy in general. Any disruption of maritime supply has significant implications on economic activity and world trade.
A sea-borne terrorist incident […] would impact heavily on the availability and cost of marine insurance.
In addition to increased insurance and re-insurance costs a catastrophic sea-borne terrorist attack would cause delays in shipping or at best, increase transit times for commodity movements.
Nowhere is this better illustrated than in the BBC News last year, when the attacks by Somali pirates made shipping companies consider whether to take the long route around Africa instead of the Suez Canal, something which overnight would have added several weeks to the lead time of shipments already underway…right before the Christmas rush. Not something you would want to happen if you were planning on selling out your (not yet arrived) stock for Christmas.
Complex systems, complex vulnerabilities
Ports have become a critical infrastructure within trading systems, and many ports are classified as hub ports that are essential both nationally and internationally for today’s global supply chains. Consequently, the threat of loss of a substantial port or substantial facilities within any port is a major issue in the protection of critical infrastructures. Ports are not just the physical infrastructure; a myriad of organizations, functions, transport modes, government agencies and freight operations meet in the port area and vulnerabilities may exist on-shore as well as off-shore (on-board).
This paper defines vulnerability as
the susceptibility or predisposition to change or loss because of existing organizational practices or conditions
and describes two types of vulnerabilities within maritime supply chains:
Type 1 vulnerability emerges from the operational complexity within a port, encompassing the transport node infrastructure and onsite operators, where cargo is transferred from one mode to the other.
Type 2 vulnerability is an attribute of maritime movements with ports as nodes in the system and global logistics management practices underpinning the supply chains operating across marine environments.
In port, these two vulnerabilities converge, in fact, they must converge and meet if a coordinated security regime both in port and out out of port is meant to work properly, i.e. securely. Without a convergent footprint a security gap may occur.
Conclusion
While this paper is not an easy read, I found it slightly unstructured, the conclusion is clear: Maritime security depends on the implementation of the treaty mandated ISPS code and the voluntary CSI and C-TPAT initiatives at operational ports.
How these programs are implemented are at the nexus of enuring security in global supply chains while pursuing business efficiency. It is arguable that as the post-modern world evolves, achieving the former is at the expense of the latter.
Perhaps the authors are right. I do remember the ISPS code being a hotly debated issue when it was implemented in the small costal town I am living in. However, the discussion seems to have abated, so maybe businesses have adapted and internalized the costs without sacrificing efficiency?
Reference
BARNES, P., & OLORUNTOBA, R. (2005). Assurance of security in maritime supply chains: Conceptual issues of vulnerability and crisis management Journal of International Management 11 (4), 519-540.DOI: 10.1016/j.intman.2005.09.008
Author Links
- qut.edu.au: Paul Barnes
- qut.edu.au: Richard Oloruntoba
Related
- husdal.com: Can pirates bring down European supply chains?