 How does the Norwegian Public Roads Administration NRPA assess the vulnerability of the Norwegian road network? This is the first post in an attempt at resurrecting this blog from its hibernating state that has now lastet for some 18 months., and marks the start of blog posts form my life as senior adviser in contingency planning and crisis management, where I spend much of my working hours developing tools for risk analysis and giving lessons on how to conduct risk analyses. The inspiration for this post is taken from the course material I prepared for a recent course.
How does the Norwegian Public Roads Administration NRPA assess the vulnerability of the Norwegian road network? This is the first post in an attempt at resurrecting this blog from its hibernating state that has now lastet for some 18 months., and marks the start of blog posts form my life as senior adviser in contingency planning and crisis management, where I spend much of my working hours developing tools for risk analysis and giving lessons on how to conduct risk analyses. The inspiration for this post is taken from the course material I prepared for a recent course.
Why risk and vulnerability analysis?
As a government body, the NRPA adheres to many laws and rules, and is guided by a number of policies and principal documents. One of these documents, the National Transport Plan, or NTP in short, states that the national goal for transport is:
To provide an efficient, accessible, safe and environmentally friendly transport system that covers society’s requirements and encourages regional development.
with accessibility being one of four main goals, as described here:
Our transport policy is to improve traffic flow and reduce the time of travel in order to strengthen competitiveness of industry and contribute to maintaining the main features of existing settlement patterns.
The most recent NTP 2014-2023 emphasizes reduced vulnerability and more adaptation to climate change as an important issue for the future:
Precipitation, temperature and wind have a strong impact on transport infrastructure and traffic management. Extreme weather, with strong winds, storm surges, heavy rains and temperature fluctuations, imposes increased demands on infrastructure. Large sections of the current transport network are not sufficiently resilient to withstand such increased strains. The infrastructure must be made more robust and emergency preparedness must be improved.
The NRPA has its own bylaw, describing in detail which tasks that we are responsible for doing, and with accessibility closely linked to vulnerability, it is no wonder then that risk analysis and contingency planning (among many other tasks) is mentioned specifically:
The NRPA is to have an overview of the threats to and the vulnerability of the road network, and work across its own organsation (and together with other agencies) in necessary contingency planning in order to ensure the best possible accessibility under changing conditions and/or possible or actual threats.
Being able to see, evaluate and manage potential risks and vulnerabilities is in fact part of the NPRA’s obligation towards society.
Societal security and business continuity
The background for this obligation can be found in the term “Societal security”, a term not very common outside of Norway. “Societal security”, which I tried to explain in a previous post, is best translated as the ability that a society has to persist under strenuous circumstances, to maintain important functions, and to provide the necessary services to uphold the life, health and welfare of its members.”It is very similar to the Finnish “security of supply” that I wrote about some time ago.
For the NRPA societal security, or “samfunnssikkerhet” in Norwegian, means the ability that we (the NRPA) has to to persist under strenuous circumstances, to maintain important functions, and to provide the necessary transport network so that society can persist. Since we plan, build, operate and maintain the Norwegian road network, it is our duty to make sure that it is functioning and accessible 24/7, even during worst of times. That is the obligation that we have towards society.
This obligation towards “societal security” is apparently so important in today’s world that the ISO in 2013 published an international standard, ISO 22301 – ″Societal Security — Business continuity management systems”, as a response to governments and regulators beginning to recognize the role of business continuity in mitigating the effects of disruptive incidents on society.
This is also reflected in Helen Peck’s 2006 article on Reconciling supply chain vulnerability, risk and supply chain management, where Peck refers to the UK Civil Contingencies Act of 2004 that requires the undertaking of business continuity planning and risk management from local government authorities, utilities providers and commercial organizations with responsibilities for essential public transport and critical infrastructure.
Risk and vulnerability
Back to risk and vulnerability, according to ISO 31000 Risk Management, there is no distinction between risk analysis and vulnerability analysis, it’s just risk analysis. However, for reasons that I cannot really understand, in Norway we mostly call it risk and vulnerability analysis. Linking risk and vulnerability is difficult. Where does one end and the other start? In my understanding, I usually use these definitions:
Risk is the potential likelihood that an event will occur and the potential consequences if the event occurs.
Vulnerability is the ability that an object has to withstand the effects of an (unwanted) event and to resume its original condition or function after that event.
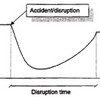
Hence, to me, risk is associated with the immediate consequences of an event, while vulnerability is associated with the extent of the ability to manage or handle the wider consequences and long-term effects rather than the imminent consequences. Essentially, the less you can handle, the more vulnerable you are. Or, to use the term business continuity, vulnerability is that which stops business from continuing.
Example: Risk: A bridge is prone to being closed because of frequent flooding. Vulnerability: There is no diversion route.
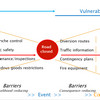
I often use the bow-tie figure below to illustrate the difference between risk and vulnerability, and between proactive and reactive measures, i.e. mitigative actions and contingent actions..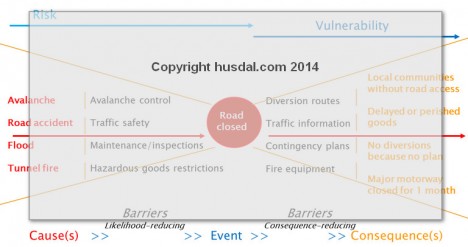
Please note that the consequence in the right column does not necessarily relate directly to the cause on the same line in the left column. Also note that the consequences illustrate the wider effects on society, i.e. the business continuity issues related to societal security, whereas the event is the immediate effect resulting from the cause(s).
ISO 31000 Risk and Vulnerability Analysis
The risk and vulnerability process in the NRPA follows the terms and steps (5.3 to 5.5) used in ISO 31000, as described in the figure below: 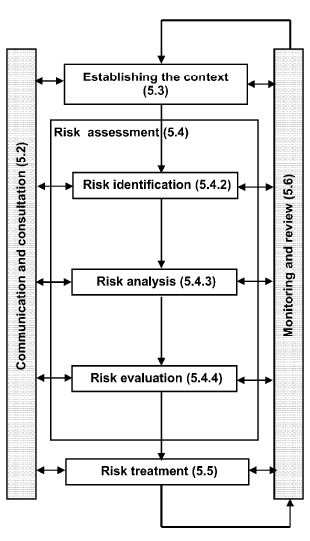 While ISO 31000 describes very well what is meant by these terms, I have made my own a bit more hands-on descriptions for what a risk and vulnerability analysis contains:
While ISO 31000 describes very well what is meant by these terms, I have made my own a bit more hands-on descriptions for what a risk and vulnerability analysis contains:
What Values do we have? Establishing the context 5.3
What do we want to protect? What can we accept?
What are the Threats we face? Risk identification 5.4.2
What are our challenges? What can go wrong? What do we fear?
What are the Likelihood and Consequences of events? Risk analysis 5.4.3
Why and how can things go wrong? Causes, drivers and results?
How is our Vulnerability and Robustness? Risk evaluation 5.4.4
If things go wrong, how bad is it really? Can we cope (or not)? What are the wider effects?
Which Likelihood-reducing measures are there? Risk treatment 5.5
What have we done (and what more can we do) to prevent things from happening?
Which Consequence-reducing measures are there? Risk treatment 5.5
What have we done (and what more can we do) to prevent things from getting worse, if they indeed do happen?
Perhaps not the best of descriptions, but they work for me.
Three levels of analysis
As to the risk and vulnerability analysis itself, it is done at three different levels: simple, simplified and detailed. Simple analysis (Level 1):
A risk and vulnerability analysis that is used to identify what risks and vulnerabilities that exist and to make initial easement of how they should be treated. The analysis shall point at possible challenges and solutions, and is a mostly qualitative analysis, a best guess or estimate.
Evaluation criteria: Best judgement
- Situation OK, risk treatment can be done if desired, but is not required.
- Situation NOT OK, risk treatment is necessary and should be done, it is not required, but highly recommended.
- Situation NOT OK AT ALL, i.e. unacceptable, risk treatment is required and must be done.
Simplified analysis (Level 2)
An extended risk and vulnerability analysis that is used to evaluate risk and vulnerability, when or where the first analysis does yield conclusive results or when or where there is a need for a more thorough analysis to evaluate different risks and risk treatments. This is a mostly quantitative analysis that aims at determining more precise values for likelihoods and consequences.
Evaluation criteria: Risk matrix 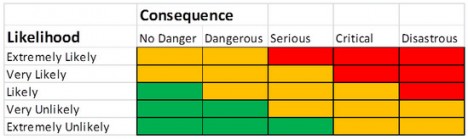
Note that this is a generic matrix and that one must decide on which values and increments to use for likelihood and consequence before starting the analysis, by answering the question “What can we accept?” when establishing the context. This also establishes the colour grading of the matrix, which may or may not be as seen above. Being generic, this matrix should be extended to include analysis-specific consequence categories, as seen in this book on Security Risk Management, e.g. consquences for people’s life/health, environment, accessibility, property/equipment.
Detailed analysis (Level 3)
A special risk and vulnerability analysis that is used to analyse specific risks and vulnerabilities, e.g. in the construction and design details of roads, bridges and tunnels. This is a detailed and quantitative analysis using statistical methods and forecasting tools aimed at ruling out any missed uncertainties in the previous levels of analysis.
Evaluation criteria: analysis(object)-specific This type of analysis is not often used within the NRPA and mostly contracted out to consultants and risk analysis experts.
Events
Obviously, there are many events that could close down a road, too many to think of, actually. That is why the NRPA risk and vulnerability analysis guidelines lists a set of “standard” events for which a road should be analysed, in order to generate a risk profile.
- Adverse weather
- Bridge closed
- Drainage failure
- Electricity blackout
- Ferry link failure
- Fire (in objects on or near the road)
- Flooding
- Foundation failure
- Frequent accident point
- Hazardous goods accident
- High winds
- Landslide (earthflow)
- Malicious actions/terrorism
- Quick clay slide
- Restrictions (in height, width, weight, axle load etc. that make the road inaccessible to some vehicles, typically Heavy Goods Vehicles)
- Road rescue and towing (of Heavy Goods Vehicles, other car rescues are neglible)
- Rockfall
- Snow avalanche
- Storm surge
- Terrain sinking (non-slide)
- Transport hub inaccessible
- Tunnel closed
In a later post I will present some of the analyses done in my work region and the risk profiles they resulted in. It is quite interesting to see which events that are most frequent in which areas.
Summary
This post was meant to give some basic insight into how the Norwegian Public Roads Administration NRPA assesses the vulnerability of the Norwegian road network. It will be followed up by more detailed posts.
Author’s note
This is my first post for some 18 months now, and it has taken me more time than expected to write this. Not just because of the language barrier, as the original material for this post is in Norwegian, but also because of a “writing barrier”. Wording and phrasing and structuring a blog post is a skill that needs regular training and I must admit that my skills are still a bit rusty. Nonetheless, there’s more to come.
Links
- iso.org: Societal security – Business continuity
- ntp.dep.no: NTP – Norwegian government whitepapers in English
Related
- husdal.com: World’s richest country – world’s worst road network
- husdal.com: Risk society