Openness, partnering, trust and particularly sharing of information has often been cited as one way to reduce supply chain risk. The more you know, and know early enough, the less surprised you may be about unforeseen developments. However, information sharing has its own set of risks. Information risks management in supply chains: an assessment and mitigation framework by Mohd Nishat Faisal, D.K. Banwet, and Ravi Shankar provides a well-founded theoretical framework for assessing these risks.
Openness, partnering, trust and particularly sharing of information has often been cited as one way to reduce supply chain risk. The more you know, and know early enough, the less surprised you may be about unforeseen developments. However, information sharing has its own set of risks. Information risks management in supply chains: an assessment and mitigation framework by Mohd Nishat Faisal, D.K. Banwet, and Ravi Shankar provides a well-founded theoretical framework for assessing these risks.
Two-in-one
Two approaches to risk assessment are used in this paper: First, interpretive structural modelling (ISM) is employed to understand the interrelationships among the enablers of information risks mitigation, resulting in a driving power and dependence matrix. Secondly, graph theory is used to quantify information risks. Unfortunately, unless I missed it somewhere, the paper provides little linkage between the two approaches.
Interdependence – Twelve enablers
In developing the driving power and dependence matrix, the authors come up with 12 “enablers” that contribute towards the mitigation of information risks:
(1) Information sharing among supply chain (SC) partners.
(2) Supply chain wide strategies to mitigate information risks.
(3) Level of supply chain integration.
(4) Collaborative relationships among supply chain (SC) partners.
(5) Support to partners.
(6) Reliable IT/IS infrastructure.
(7) Top management commitment.
(8) Trust among supply chain (SC) partners.
(9) Awareness about information risks.
(10) Availability of funds to implement information risk mitigation strategies.
(11) Incentives alignment.
(12) Metrics for continual information risks assessment and analysis.
Through a set of operations, linking enabler i (e.g. #2 above) with enabler j (e.g. #4 above) ,the relationship between each enabler is investigated, e.g.
(1) enabler i will help to achieve enabler j.
(2) enabler i will be achieved by enabler j.
(3) enabler i and j will help achieve each other.
(4) enablers i and j are unrelated.
Cutting a long story short, in the end they reach the following conclusion:
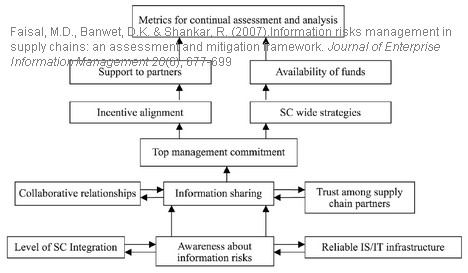
Driving power and dependence
The above is then presented as a matrix:
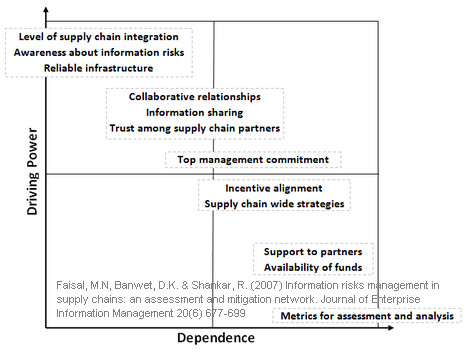
The enablers are further classified as
(1) Autonomous enablers (Southwest quadrant)
(2) Dependent enablers (Southeast quadrant)
(3) Linkage enablers (Northeast quadrant)
(4) Independent enablers (Northwest quadrant)
Autonomous enablers have a weak driver power and weak dependence. These enablers are relatively disconnected from the system. Dependent enablers are dependent on the other variables. Linkage variables work both ways; they affect the enablers above and are at the same time dependent on the enablers below. Independent variables have a strong driver power and weak dependence. These enablers are the most important variables and appear at the top of the ISM hierarchy, implying that management needs to address these enabler variables more carefully than perhaps the other enablers.
Quantification of risks – graph theory
I have chosen to deliberately skip this part of the paper in my review. Not because it is not interesting, but because it appears as a separate part unrelated to the aforementioned. Personally, if I were the author, I would have split this one paper into two separate papers; one paper using the interpretive structural modelling and another paper using graph theory. The way it is now I see a mixing, not a linking, of two separate approaches.
Conclusion
The article highlights that information risks are interrelated and that one factor (or “enabler”) cannot be mitigated without taking into account all the other factors that contribute to or are dependent on this factor. This is similar to the argument on corporate vulnerability in Svensson (2004), where
Corporate vulnerability may be influenced by the current and potential direct and indirect dependencies, the vertical and horizontal dependencies, as well as the unidirectional and bi-directional dependencies, between business activities in and between supply chains.
The article also reflect some of the points made in Christopher and Lee (2004) on supply chain confidence, where the argument is made that
Total end-to-end visibility will enable supply chains to be transparent, and the right information would be available to the right member of the supply chain at the right time.
This paper identifies twelve variables which may help mitigate information risks in supply chains. I may not agree with these twelve as such. Maybe there should be more, maybe less. Nonetheless, the approach used in the paper is worth looking into.
Reference
Faisal, M., Banwet, D., & Shankar, R. (2007). Information risks management in supply chains: an assessment and mitigation framework Journal of Enterprise Information Management, 20 (6), 677-699 DOI: 10.1108/17410390710830727
Author links
- qu.edu: Mohd Nishat Faisal
- researchgate.net: D.K. Banwet
- researchgate.net: Ravi Shankar
Related
- husdal.com: Supply Chain Confidence
- husdal.com: Corporate vulnerability