 A new outlet for articles on supply chain vulnerability? Perhaps. And actually, it’s not that new, since the journal has been in existence for some 16 years, but I haven’t come across the Journal of Marketing Channels as a source for papers on supply chain disruption before. That is why I was so surprised to find Sources of Supply Chain Disruptions, Factors That Breed Vulnerability, and Mitigating Strategies by Karen E Stecke and Sanjay Kumar. Here they develop a classification framework for supply chain catastrophes and the appropriate mitigation strategies for the various types of smaller and bigger supply chain disasters that can occur.
A new outlet for articles on supply chain vulnerability? Perhaps. And actually, it’s not that new, since the journal has been in existence for some 16 years, but I haven’t come across the Journal of Marketing Channels as a source for papers on supply chain disruption before. That is why I was so surprised to find Sources of Supply Chain Disruptions, Factors That Breed Vulnerability, and Mitigating Strategies by Karen E Stecke and Sanjay Kumar. Here they develop a classification framework for supply chain catastrophes and the appropriate mitigation strategies for the various types of smaller and bigger supply chain disasters that can occur.
Supply chain components
A disaster affects a supply chain by affecting one or more of its components. These components are either internal or external to the supply chain, and can be classified as belonging to the following realms or contributors to the functioning of the supply chain:
- Transportation
- Utilities/Equipment
- Communication
- Suppliers
- Customers
- Labor
- Finance
Stecke and Kumar only see two sides of the supply chain, the internal side and the external side. While I find this a simplification of Christopher’s supply-demand-process-enviroment framework for supply chain risks, it is still valid.
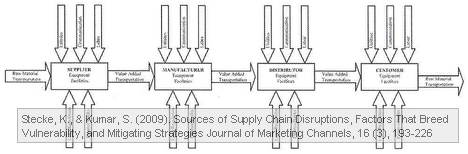
What I find interesting is the selection of components they have attached to the supply chain; very few papers I have seen have included transportation or finance and labor in the equation.
Vulnerability factors
Current supply chain trends have made supply chains more efficient, but unfortunately also made supply chains more vulnerable, so says Martin Christopher in his book chapter on supply chain risk:
- The trend towards just in time and lean practices
>>> efficiency rather than effectiveness - The trend towards reducing costs
>>> globalization, more complex and longer supply chains - The trend towards economies of scale
>>> centralized distribution and manufacturing
>>> lower costs, but also less flexibility - The trend towards outsourcing of non-core business activities
>>> loss of control when it is most needed - The trend towards consolidation of suppliers
>>> increased potential for wider impacts of disruptions
Stecke and Kumar add to this list by identifying
- Globalization
- Decentralization
- Outsourcing
- Sole sorcing
- Just-in-Time
- Product complexity
- Litigation
as key supply chain management practices that breed vulnerability by creating
- an increase in the number of exposure points
- an increase in distance and time
- a decrease in flexibility
- a decrease in redundancy
which in end may cause supply chain catastrophes.
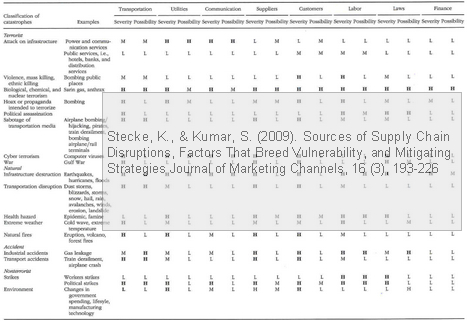
Supply chain catastrophes
The list of possible supply chain disruptions reveals a penchant for Paul Kleindorfer’s catastrophic events or Nassim Taleb’s black swans; some of the examples used are:
- Terrorist attacks
- Mass killings
- Political assassinations
- Sabotage of infrastructure
- Natural disasters
- Earthquakes
- Extreme weather
- Epidemic
- Accidents
- Industrial fire
- Gas leakage
- Train derailment
- Plane crash
- Non-terrorist
- Strikes and labor disputes
- Environment
- Changes in rules and regulations
- New technology
Terrorism or malicious attacks make up most of the list, and considering that global supply chains are increasingly sourcing from politically potentially unstable countries, they should rightly be at the top of the list.
Catastrophe mitigation
- Proactive strategies
- Select safe locations
- Chose robust suppliers and transportation media
- Establish secure communication links
- Enforce security
- Advance warning strategies
- Enhance visibility and coordination
- Increase transportation visibility
- Monitor weather forecasts
- Act according to terrorist threat level
- Monitor trends
- Coping strategies
- Monitor multiple facilities hat have flexible/redundant resources
- Cary extra inventory
- Arrange for alternative sourcing
- Ensure flexible transportation
- maintain redundant critical components
- Redesign products to pool risks
- Influence customer choice
- Purchase insurance cover
While it does not appear in their reference list, much of the above can also be found in Christopher Tang’s Robust strategies for mitigating supply chain disruptions.
Benefits
The article also list some of the benefits of mitigating supply chain disruptions:
- Reduction of lead time and lead time variability
- Better inventory management
- Efficient production planning and forecasting
- Reduction of the bullwhip effect
- Increase in customer service
- Better demand management
Incidentally, this list is not so unlike the report on the collateral benefits of supply chain security by he IBM Center for the Business of Government.
Table, tables , tables
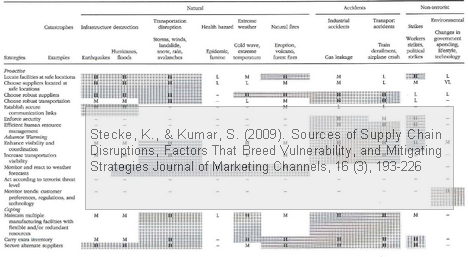
What I really like about this paper is the effort they have put into making systematic tables of how everything in supply chains relates to each other, where each factor is graded on a low-medium-high scale. First, there is a table relating each of the catastrophe types to the supply chain components, and the likelihood of impact and severity of impact on each component.
The second table looks at which mitigation strategy that works best when faced with which catastrophe.
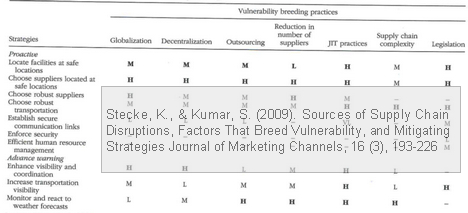
The third table shows what impact each strategy has on each of the factors that breed vulnerability.
It is easy to lose oversight here, but nothing is left out, for sure.
Conclusion
This is indeed one of the most comprehensive papers I have found on supply chain vulnerability and mitigation strategies. While many of the suggestions in the tables are based on expert judgement, and thus subjective, I found it to be a sound expert judgement. Although naming the strategies as mitigation strategies, many of them are just as much contingent as they are mitigative. This is a hands-on paper with significant managerial implications, clearly outlining and identifying a number of strategies and where they are applicable, making this a paper that perhaps is just as much or perhaps even more suited for a professional audience than an academic audience. It is a paper that every supply chain manager should read, at least once.
Reference
Stecke, K., & Kumar, S. (2009). Sources of Supply Chain Disruptions, Factors That Breed Vulnerability, and Mitigating Strategies Journal of Marketing Channels, 16 (3), 193-226 DOI: 10.1080/10466690902932551
Author links
- linkedin.com: Kathryn E Stecke
- linkedin.com: Sanjay Kumar
Related
- husdal.com: Mitigative and contingent actions
- husdal.com: Black Swan Events
- husdal.com: Managing risk in global supply chains