This is a paper that has been collecting dust in my articles archive for quite a while, but it is indeed a paper that shouldn’t be hidden to the readers of my blog and it deserves to be promoted. The reason why I like it is because it adopts a holistic approach to model the interconnectedness and interdependencies of infrastructure systems. Infrastructure Risk Analysis Model, written by Barry C Ezell, John V Farr and Ian Wiese and published in 2000 describes an infrastructure risk analysis model that in a straightforward engineering manner considers possible threats, potential impacts and their mitigation.
This is a paper that has been collecting dust in my articles archive for quite a while, but it is indeed a paper that shouldn’t be hidden to the readers of my blog and it deserves to be promoted. The reason why I like it is because it adopts a holistic approach to model the interconnectedness and interdependencies of infrastructure systems. Infrastructure Risk Analysis Model, written by Barry C Ezell, John V Farr and Ian Wiese and published in 2000 describes an infrastructure risk analysis model that in a straightforward engineering manner considers possible threats, potential impacts and their mitigation.
Systematic and solid
The model follows the commonly accepted risk assessment method of fault and event trees. Exposure and access serve as an initial measure of vulnerability that requires further investigation and assessment, implying malevolence and security threats as their main cause for concern.
The model provides a systematic process to conduct vulnerability modelling, assessment and management across different infrastructures, allowing for rank-ordering of alternatives and scenario bounding.
IRAM
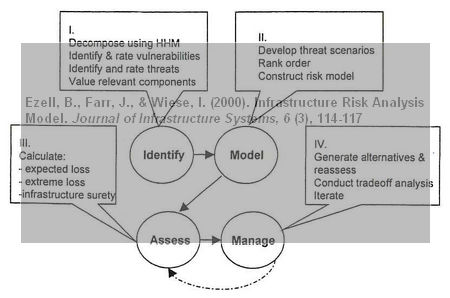
The Infrastructure Risk Analysis Model, or IRAM as they call it, consists of four stages:
- Identify risks by first decomposing the system using hierarchical holographic modeling. Result: a rank order of vulnerabilities for further assessment.
- Develop scenarios. Result: a probabilistic model containing the risk for each scenario.
- Assess scenarios. Result: a calculation of infrastructure surety, extreme loss and expected loss.
- Manage scenarios and predict infrastructure performance. Result: a multiobjective tradeoff analysis.
These four steps ensure a systematic process for risk modelling, assessment and management. The four steps, so the authors claim, are an exhaustive taxonomy, i.e. all that is needed.
Regardless of the infrastructure, the system can be decomposed using a systems perspective. Once decomposed, vulnerability can be assessed using a rigorous analysis of exposure and access, through a multitude of ranking and filtering technologies to bound the scenarios into rank order alternatives. Event trees and fault trees are expedient and proven tools for probabilistic modelling. By modelling expected as well as extreme risk, IRAM provides the decision maker with outcomes for both normal and unusual loading of the system. Finally, a multiobjective tradeoff analysis helps decide the best alternative.
At least from the looks of it, it does seem like a straightforward and easy-to-follow process.
Critique
The beauty of this paper is that it is so easy to follow. While a small shortcoming is that it focuses on water supply only, this type of analysis can be applied universally to any type of interconnected infrastructure elements such as physical facilities, electric power generation and distribution, and telecommunications. I believe that many will find this model very useful, e.g. insurance companies, municipal managers, utility companies, etc., who can use this technique to develop scenarios and quantify the value of countermeasures. Interestingly enough, though, I haven’t seen this paper referenced too often in other papers. I think it should, another reason for why I am promoting it.
Whatever happened to…?
Regular readers of my blog will know that I always include links to the authors of the papers I review wherever possible. Usually, if the paper is not too dated, this is easy. This paper, however, is 10 years old, and presumably the authors are no longer affiliated with what the paper lists as their affiliation (e.g. university or research institute). Nonetheless, with the help of the right keywords in Google I was able to track down two out of three. If anyone has any information on the last guy, please let me know. Thanks.
Reference
Ezell, B., Farr, J., & Wiese, I. (2000). Infrastructure Risk Analysis Model Journal of Infrastructure Systems, 6 (3), 114-117 DOI: 10.1061/(ASCE)1076-0342(2000)6:3(114)
Author links
- innovativedecisions.com: Barry C.Ezell
- stevens.edu: John V Farr
- Ian Wiese