A tip-off
A couple of weeks I was given a heads-up by one of the authors that they had written a paper called Towards an Integrated Model of Supply Chain Risks: an Alignment between Supply Chain Characteristics and Risk Dimensions and would like my opinion on it. Written by Arij Lahmar, Francois Galasso, Habib Chabchoub and Jacques Lamothe, the paper turned out to be more interesting than I first thought, and the more I read it the more I liked it.
Virtual Enterprises revisited
What also intruiged me into taking a closer look at the paper was not so much the title, but the place where it was presented, namely the IFIP WG 5.5 Working Conference on Virtual Enterprises. Observant readers of this blog may remember that I 5 years ago wrote a book chapter titled A Conceptual Framework for Risk and Vulnerability in Virtual Enterprise Networks, where I extended Supply Chain Risk Management into the realm of Virtual Enterprise Networks. I’ve seen that chapter mentioned as a reference in some of the papers presented at IFIP conferences earlier, and I first thought this would be such an example, too. It was not; it was something quite different.
SCRM versus SCRIM
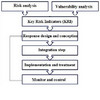
As the title implies, at the heart of the SCRIM model is the alignment of risk dimension with suply chain characteristics. Here risk specifics and supply chain specifics are used to develop key risk indicators that lead to the design of a response that is specific to the supply chain and the risk in question. The possible response is then checked against capabilities to decide the best risk mitigation strategies and actions, in a sort of Plan-Do-Check-Act manner:
From my point of view this conceptual model appears sound. The left side is the traditional SCRM and ISO 31000 process, the right side is the new concept. The figure could have been a bit more descriptive, though, because the steps on the right side did not become fully clear to me until I saw the other figure in the paper. That figure is a class model detailing the parameters identified through the literature:
However, agin, this figure too has a few shortcomings. While the model claims to be taken from an extensive literature review – and judging from the extensive reference list it indeed is – the paper does not explicitly state which references that have contributed to which part of the figure.
For one instance, as risk strategies they suggest the classic four: Reduce, Retain, Avoid and Transfer, but where does this idea come from? For another instance, capability is seen as important part of the risk treatment process, and I agree, but the concept of capability is poorly described in the paper.
Conclusion
Essentially this is a good paper that needs some revision of references and citations and consistent use of the terms involved. It also needs fuller definitions of the concepts that are introduced.
That said, this paper does develop a new conceptual model that brings SC in more direct contact with RM, and SCRIM is indeed a fitting name for the model. The model and parameter description is perhaps still not complete in all parts, but with some more refinement this could definitely bring SCRM a huge step forward.
Reference
Lahmar, A., Galasso, F., Chabchoub, H., Lamothe, J. (2015) Towards an Integrated Model of Supply Chain Risks: an Alignment between Supply Chain Characteristics and Risk Dimensions. In: L. Camarinha-Matos, F. Bénaben, W. Picard (Eds.) Risks and Resilience of Collaborative Networks, Proceedings of the 16th IFIP WG 5.5 Working Conference on Virtual Enterprises, PRO-VE 2015, Albi, France, October 5-7, 2015 DOI: 10.1007/978-3-319-24141-8_1
Author links
- linkedin.com: Arij Lahmar
- linkedin.com: Francois Galasso
- linkedin.com: Habib Chabchoub
- linkedin.com: Jacques Lamothe
Related posts
- husdal.com: ISO 31000 Risk Management