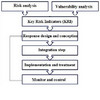
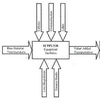
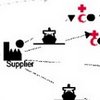
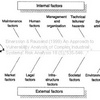
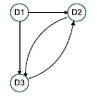
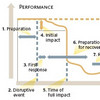
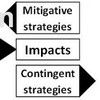
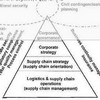
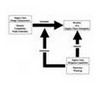
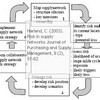
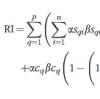This paper develops a new conceptual model that brings SC in more direct contact with RM, by incorporating vulnerability to develop the key risk indicators,thus linking potential risk with actual risk.
- ARTICLES and PAPERS
- BOOKS and BOOK CHAPTERS
- REPORTS and WHITEPAPERS
- LITERATURE Reviews A-Z
- Literature Review – A
- Literature Review – B
- Literature Review – C
- Literature Review – D
- Literature Review – E
- Literature Review – F
- Literature Review – G
- Literature Review – H
- Literature Review – I
- Literature Review – J
- Literature Review – K
- Literature Review – L
- Literature Review – M
- Literature Review – N
- Literature Review – O
- Literature Review – P
- Literature Review – Q
- Literature Review – R
- Literature Review – S
- Literature Review – T
- Literature Review – U
- Literature Review – V
- Literature Review – W
- Literature Review – X
- Literature Review – Y
- Literature Review – Z
- EVERYTHING else