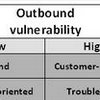
In ‘A conceptual framework of vulnerability in firms’ inbound and outbound logistics flows.’, Göran Svensson separates inbound and outbound flows, adds 2 categories of disturbance (quantitative and qualitative), and also adds 2 sources of disturbance (atomistic and holistic) create 4 vulnerability scenarios.
- ARTICLES and PAPERS
- BOOKS and BOOK CHAPTERS
- REPORTS and WHITEPAPERS
- LITERATURE Reviews A-Z
- Literature Review – A
- Literature Review – B
- Literature Review – C
- Literature Review – D
- Literature Review – E
- Literature Review – F
- Literature Review – G
- Literature Review – H
- Literature Review – I
- Literature Review – J
- Literature Review – K
- Literature Review – L
- Literature Review – M
- Literature Review – N
- Literature Review – O
- Literature Review – P
- Literature Review – Q
- Literature Review – R
- Literature Review – S
- Literature Review – T
- Literature Review – U
- Literature Review – V
- Literature Review – W
- Literature Review – X
- Literature Review – Y
- Literature Review – Z
- EVERYTHING else

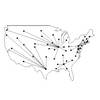







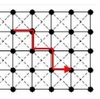 Locating a right-of-way for a linear facility such as a pipeline, a transmission line, a railway or a roadway can be a complex problem. Locating a corridor connecting an origin and a destination on a landscape is analogous to identifying a route that traverses a continuous landscape. Thus, corridor analysis is closely linked to shortest-path finding and network analysis in
Locating a right-of-way for a linear facility such as a pipeline, a transmission line, a railway or a roadway can be a complex problem. Locating a corridor connecting an origin and a destination on a landscape is analogous to identifying a route that traverses a continuous landscape. Thus, corridor analysis is closely linked to shortest-path finding and network analysis in 












